
The future of quantum computing
China’s Micius satellite is an impressive leap forward in the realm of quantum computing, but viable quantum capabilities remain years away
On August 16, 2016, the People’s Republic of China (PRC) launched a satellite equipped with quantum communication capabilities, marking a new stage in the development of information security.1 Representing the first attempt to establish quantum communication systems between earth and space, the launch of the Micius satellite could revolutionize encryption. Chinese researchers will use the satellite to study the capabilities of quantum encryption systems.2 If the new satellite proves successful, the PRC plans to follow it with projects Micius 2 and Micius 3.3 The PRC hopes to establish a global quantum communications network by 2030.4 On November 20, 2016, the PRC completed the first phase of its planned 2,000 km quantum communication line connecting Beijing and Shanghai. The line is currently 712 km long, and connects the capital of Anhui province to Shanghai.5 While the actual functions of the line are unclear, it is the largest piece of quantum communication infrastructure in the world, establishing the PRC as a groundbreaker in applied quantum physics.6
Quantum communication systems theoretically provide near perfect security, making them superior to traditional encryption models. Information security relies on a two-pronged test: the system must be based on sound principles, and its implementation must not create vulnerabilities.7 Modern public key cryptography fails the first prong because it relies on two assumptions. First, that the private key is secure, and second, that the public key cannot be broken. Public key encryption allows the sender to encrypt information using an open source key These cyphers are extremely difficult for existing computers to break because they rely on the principle that numbers composed of very large primes are extremely difficult to factor. Theoretically, the public key is unbreakable. The weakest link in the chain is the privately held decryption key. Whoever holds this key can access any of the data being transmitted by the sender.8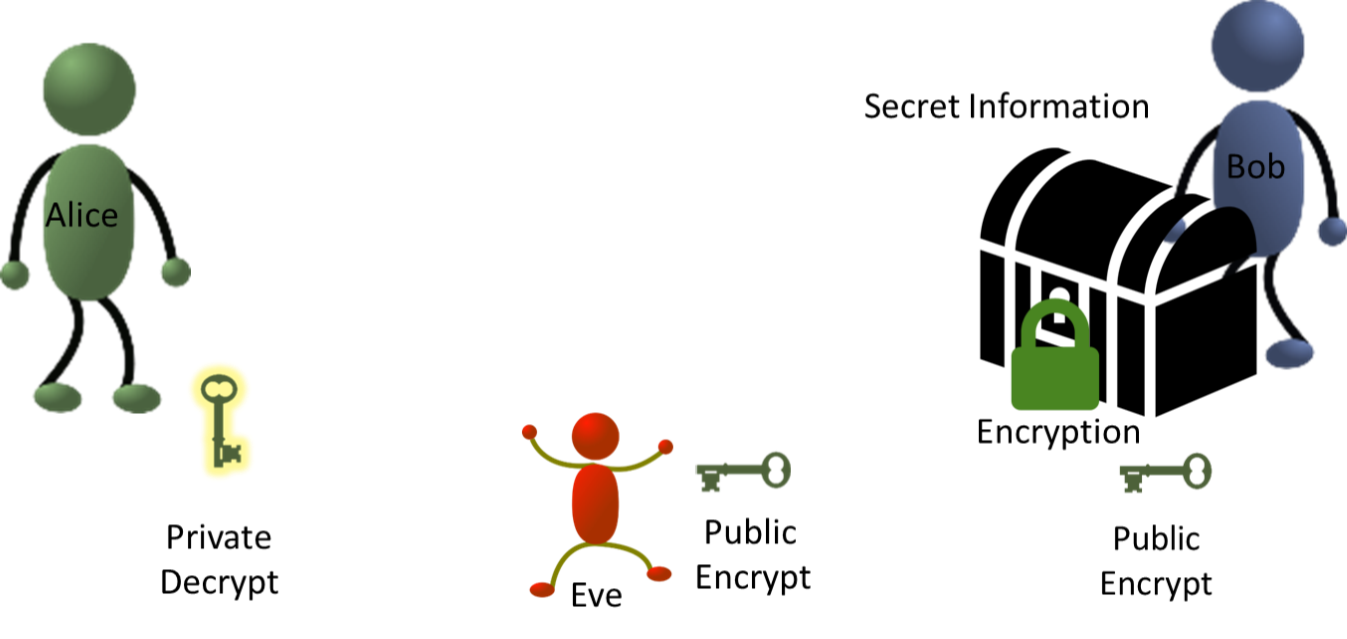
In this illustration, Bob wants to send the secret information to Alice. Using the public domain encryption key, Bob “locks” the information so that Eve cannot access it. It is irrelevant whether Eve possesses the public encryption key because it cannot be used to decrypt the information. Once the secret information reaches Alice, she uses the private decryption key which only she possesses to “unlock” the message.
This delivery system suffers from two vulnerabilities. First, it is possible that Eve could break the public encryption key. This risk becomes progressively greater as quantum computers could be developed as soon as 2025.10 Modern encryption is secure because computers can only work on one problem at a time. At that speed, it would take hundreds of years to factor an RSA key. Quantum computers can work multiple problems simultaneously, meaning that they could brute force the most advanced encryption key in a matter of seconds.11 While a practical quantum computing system remains to be developed, quantum factoring algorithms have existed since 1994.12
Eve can also access the secret information if she can intercept the private decrypt key. Secure communication channels are used to distribute private keys, but it is impossible to discern whether existing channels have been tampered with.13 Users of these channels must assume that no eavesdropper has intercepted the information.
Quantum Key Distribution (QKD) ensures the security of private communication channels. Quantum physics is governed by the Heisenberg Uncertainty Principle, which dictates that at the quantum level, one of a particle’s properties cannot be measured without altering the particle’s other properties.14 QKD uses oriented photons –packets of light to distribute private keys securely. Like bits in a computers system, these photons can be encrypted, so even if an eavesdropper intercepts the signal, he will be unable to access the information. Quantum keys are decrypted by only measuring photons with a specific orientation using a calcite crystal.15 Theoretically, the system cannot be wiretapped without Alice’s knowledge because measuring the photon stream will alter the state of the
information, rendering it unusable.16 When Alice receives a garbled decrypt key, she knows that Eve has intercepted it. Alice simply discards the useless key, switches channels, and asks Bob to send a new one. Unlike modern encryption systems, QKD relies on sound principles which guarantee an unprecedented level of security for encrypted communications.
Quantum encryption is increasingly used in government, finance, and network security. Some banks in the PRC already use quantum encryption to transmit sensitive financial information.17 The new quantum line will be used for sensitive military and government communications.18 The PRC is not the only party exploring QKD. Switzerland has used id Quantique’s QKD systems to secure election results since 2007.19 Los Alamos National Laboratory developed a quantum encrypted internet in 2011.21 In 2016, the European Commission launched a 1 billion euro initiative to research and develop quantum encryption capabilities.22
Quantum encryption is not invincible. Some analysts have lauded the new quantum capabilities as “foolproof”21 and “forever immune from hackers or malware makers.”22 This praise is overblown. While quantum encryption is perfectly secure in principle, in practice it suffers from security weaknesses. To date, the known vulnerabilities of QKD stem from its implementation. In 2011, researchers from Singapore and Norway successfully eavesdropped on a QKD while remaining undetected.24 Because QKD uses light rather than electric current to transmit information, quantum transmissions currently rely on fiber optic cables. These cables produce a certain level of interference that alters the state of some of the photons being transmitted.25 This white noise is indistinguishable from the alterations produced by an eavesdropper. Along a fiber optic cable, the most common QKD protocol, BB84, has an error rate of 11%.26 If an eavesdropper can measure the photons being transmitted without raising the error rate above that percentage, the receiver cannot know that the message was intercepted. Researchers relied on this flaw to exploit the QKD protocol.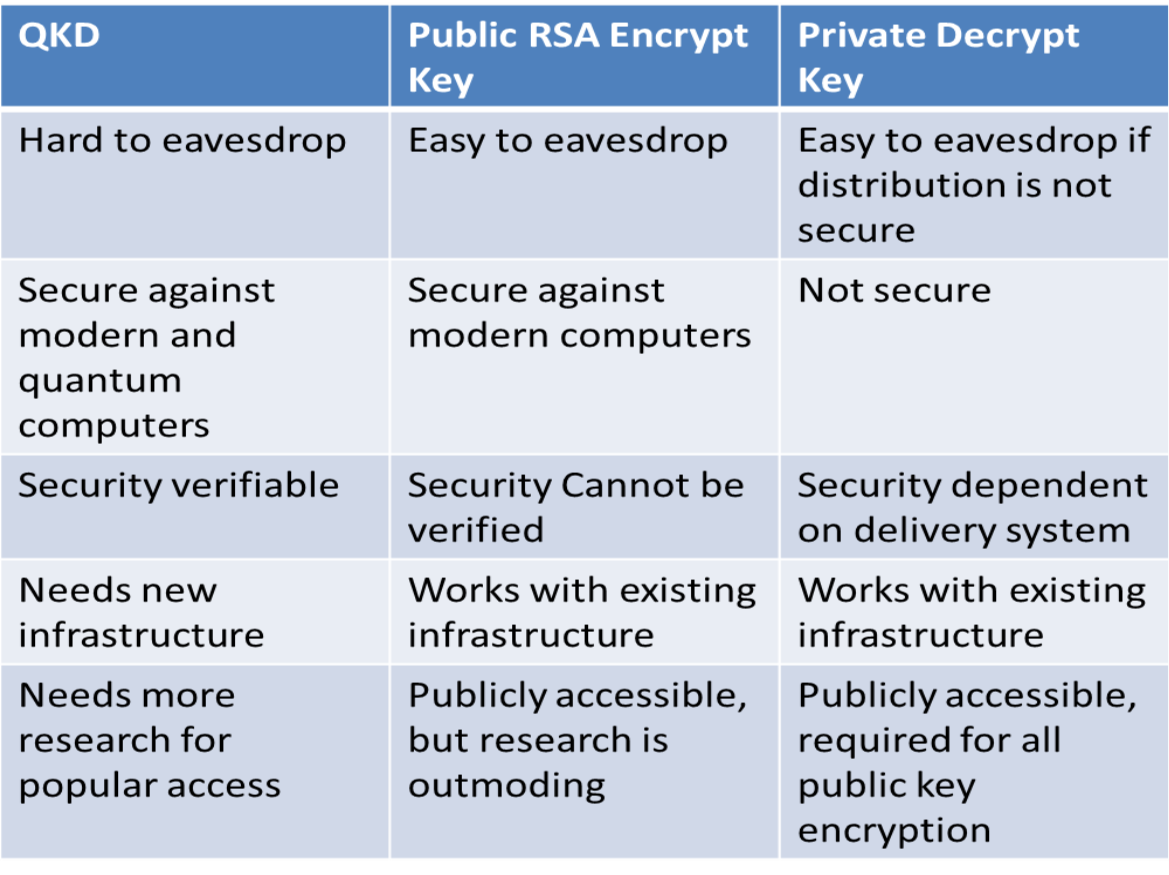
Besides structural errors, any encryption system is vulnerable to social engineering. Regardless of how much researchers can reduce the error rate of QKD protocols, the system is irrelevant if attackers can access the keys by exploiting employees of the parties involved. No amount of coding can protect information if the person holding it is compromised. It is essential that assessments of quantum cryptographic systems note these vulnerabilities.
Quantum encryption will not be widely available in the immediate future. Because of the nature of light, principally secure quantum communications can only transmit photons using either lasers, in the case of the Micius satellite, or fiber optic cables. The vast majority of internet infrastructure relies on copper wires because data is currently transmitted in bits.27 This renders QKD useless for most consumer devices. Other challenges for quantum capabilities are distance and routing. A photon travelling over a fiber optic cable can travel no farther than 500 km before becoming garbled.28 Satellite based quantum communications can travel much farther because earth’s atmosphere minimally impacts the state of photons travelling through it.29 However, because receiving stations on earth can only capture roughly one in every million photons transmitted by the satellite, they must be ten times as precise as receivers for an ordinary satellite.30 The chief commander of the PRC’s Micius program described the process as, “Like tossing a coin from a plane at 100,000 meters above the sea level exactly into the slot of a rotating piggy bank.”31 Infrastructure this precise cannot be made widely available in the foreseeable future.
The very property that makes quantum communications secure also limits their usefulness. Eavesdropping on a quantum system is difficult because reading and measuring photons alters their state. By that same property, however, those particles cannot be amplified or rerouted.32 The Los Alamos internet reroutes the quantum transmissions by translating them at a central hub, encrypting them again, and then sending them on to their destination.33 While this method makes a quantum network viable, it also resurrects the same security risks which QKD is designed to outmode. Every hub at which the transmissions are translated and rerouted becomes a chink in the armor where eavesdroppers can exploit the existing vulnerabilities of public key encryption. This could render quantum networks useless, particularly if quantum computing becomes a reality in the near future.
Quantum cryptography’s greater security justifies its development. The history of cryptography is one of groundbreaking technologies and strategic surprises. No matter how secure a communication system may appear, it will always have vulnerabilities. Especially as quantum computing continues to become more feasible, conventional encryption systems will have to be replaced. Developing threats increasingly demand quantum capabilities. The US should continue its research into QKD systems and encourage industries to shift their communications to these more secure lines. At the same time, users of QKD must be aware of the security vulnerabilities which exist in its current implementation and work to minimize them. ■
-
- 1. “China Takes Quantum Communication Leap,” Global Times, May 30, 2016,
2. Ibid.
3. “China to Send More Quantum Satellites Into Space,” BBC Worldwide Monitoring, August 16, 2016, http://www.lexisnexis.com.ezproxy.phc.edu/lnacui2api/api/version1/getDocCui?lni=5KGC-7YW1-DYRV-32PK&csi=270944,270077,11059,8411&hl=t&hv=t&hnsd=f&hns=t&hgn=t&oc=00240&perma=true.
4. “China Takes Quantum Communication Leap,” Global Times.
5. “China Launches World’s Longest Quantum Communication Line,” The Hindu, December 2, 2016, http://www.thehindu.com/news/international/China-launches-world%E2%80%99s-longest-quantum-communication-line/article16668990.ece
6. Ibid.
7. “Quantum Cryptography: Everything You Need to Know about Quantum Cryptography,” Swiss Quantum, 2009, http://swissquantum.idquantique.com/?-Quantum-Cryptography-
8. “Quantum Encryption – A Means to Perfect Security?” Sans Institute, 2003, https://www.sans.org/reading-room/whitepapers/vpns/quantum-encryption-means-perfect-security-986
9. Dr. Wallace E. Kelly, “Introduction to Cryptology,” November 17, 2016.
10. “Microsoft Lab Predicts We’ll Have a Working ‘Hybrid’ Quantum Computer in 10 Years,” Business Insider, October 22, 2015, http://www.businessinsider.com/microsoft-hybrid-quantum-computer-2015-10
11. “China Launches First-Ever Quantum Communication Satellite,” China Daily, August 16, 2016, http://www.lexisnexis.com.ezproxy.phc.edu/lnacui2api/api/version1/getDocCui?lni=5KGD-FPB1-JDJN-62PG&csi=270944,270077,11059,8411&hl=t&hv=t&hnsd=f&hns=t&hgn=t&oc=00240&perma=true
12. Lek, Kamol, and Naruemol Rajapakse, Cryptography : Protocols, Design, and Applications (Hauppauge: Nova Science Publishers, Inc, 2012).
13. “Quantum Encryption – A Means to Perfect Security?” Sans Institute.
14. Gilles Van Assche, Quantum Cryptography and Secret-Key Distillation (Cambridge: Cambridge University Press, 2006).
15. “Quantum Encryption – A Means to Perfect Security?” Sans Institute.
16. “Researchers Successfully Eavesdrop On Quantum Encrypted Communications,” Forbes, June 15, 2011, https://www.forbes.com/sites/alexknapp/2011/06/15/researchers-successfully-eavesdrop-on-quantum-encrypted-communications/#7af5076e1201
17. “China to Send More Quantum Satellites Into Space,” BBC Worldwide Monitoring.
18. Ibid.
19. “Will Quantum Encryption Arrive Before Quantum Computers Break All Our Passwords?” Forbes, April 16, 2017, https://www.forbes.com/sites/jeffmcmahon/2016/04/17/will-quantum-encryption-arrive-before-quantum-computers-guess-all-our-passwords/#5a552f38281a. Also see “Quantum Cryptography: Everything You Need to Know about Quantum Cryptography,” Swiss Quantum.
20. “Los Alamos National Lab Has Had Quantum-Encrypted Internet for Over Two Years,” Engadget, May 6, 2013, https://www.engadget.com/2013/05/06/quantum-encrypted-internet-los-alamos/
21. China Takes Quantum Communication Leap, Global Times.
22. “Will Quantum Encryption Arrive Before Quantum Computers Break All Our Passwords?” Forbes.
23. “Quantum Cryptography: A Boon for Security,” National Review, March 10, 2017, http://www.nationalreview.com/article/445663/quantum-computing-intelligence-security-improvement
24. Researchers Successfully Eavesdrop On Quantum Encrypted Communications,” Forbes.
25. S. Molotkov, “What is a quantum cryptography protocol that ensures the maximum distance in the case of a strictly single-photon source?” American Institute of Physics, October 2015, http://62PG&csi=270944,270077,11059,8411&hl=t&hv=t&hnsd=f&hns=t&hgn=t&oc=00240&perma=true
26. Ibid.
27. “Quantum Encryption – A Means to Perfect Security?” Sans Institute.
28. “China Launches First-Ever Quantum Communication Satellite,” China Daily.
29. Ibid.
30. Ibid.
31. Ibid.
32. “Quantum Cryptography: Everything You Need to Know about Quantum Cryptography,” Swiss Quantum.
33. “Commercial Quantum Cryptography System Hacked,” MIT Technology Review, May 17, 2010, https://www.technologyreview.com/s/514581/government-lab-reveals-quantum-internet-operated-continuously-for-over-two-years/
Photo Credit:
Wikimedia Commons | https://upload.wikimedia.org/wikipedia/commons/thumb/1/1a/Code.jpg/1280px-Code.jpg
Spring 2017
Volume 20, Issue 3
31 March






