
The growing threat of north Korea's global intelligence capabilities
North Korea’s first successful intercontinental ballistic missile (ICBM) test in July 2017 and assassination of Kim Jong-nam in February 2017 indicate that North Korea has very likely become more advanced and aggressive in its intelligence collection capabilities. Following the successful launch of North Korea’s Hwasong 14 ICBM, the country claimed in late August of 2017 that it had the capabilities to tip a missile with a hydrogen bomb.1 North Korea’s accelerated nuclear development may be due to an increase in the country’s intelligence collection capabilities. In order to contain North Korea’s weapons development efforts, the United States should increase its counterintelligence effort against North Korea.
The North Korean government recently reorganized and modernized its intelligence community. In addition to existing intelligence-gathering apparatus, North Korea established the Reconnaissance General Bureau (RGB) in 2010 to increase its foreign intelligence collection capabilities.2 The RGB is modeled after Russia’s Main Intelligence Directorate (GRU). According to United States Department of Defense, the RGB is North Korea’s primary service for clandestine operations and intelligence collection.3 A Pentagon report explains, “The RGB is comprised of six bureaus with compartmented functions including operations, reconnaissance, technology and cyber, overseas intelligence, inter-Korean talks, and service support.”3 It is highly probable that two North Korean clandestine operators, who attempted to smuggle nuclear secrets out of Ukraine, were trained and deployed by the RGB.4
The recently established RGB has made notable progress in the development of its cyber capabilities. Within the RGB there is a special cell called Unit 180, which is responsible for conducting all of North Korea’s cyberattacks and operations.5 According to North Korean defectors, Unit 180 is responsible for launching some of North Korea’s most dangerous and daring cyberattacks.5 Most of North Korea’s cyberattacks target financial institutions. Since the establishment of Unit 180, North Korea has hacked various financial networks within the United States, South Korea, and an estimated dozen other countries.5 As North Korea’s cyber unit continues to modernize, the attacks it conducts become more sophisticated. Symantec Corporation cyber security experts have found evidence linking North Korea to the global “WannaCry” ransomware attack of 2017 which affected over 300,000 computers globally.5 Independent of North Korea’s role in the “WannaCry” ransomware attacks, US intelligence officials have determined that North Korea poses a significant cyber threat to U.S. national security.6
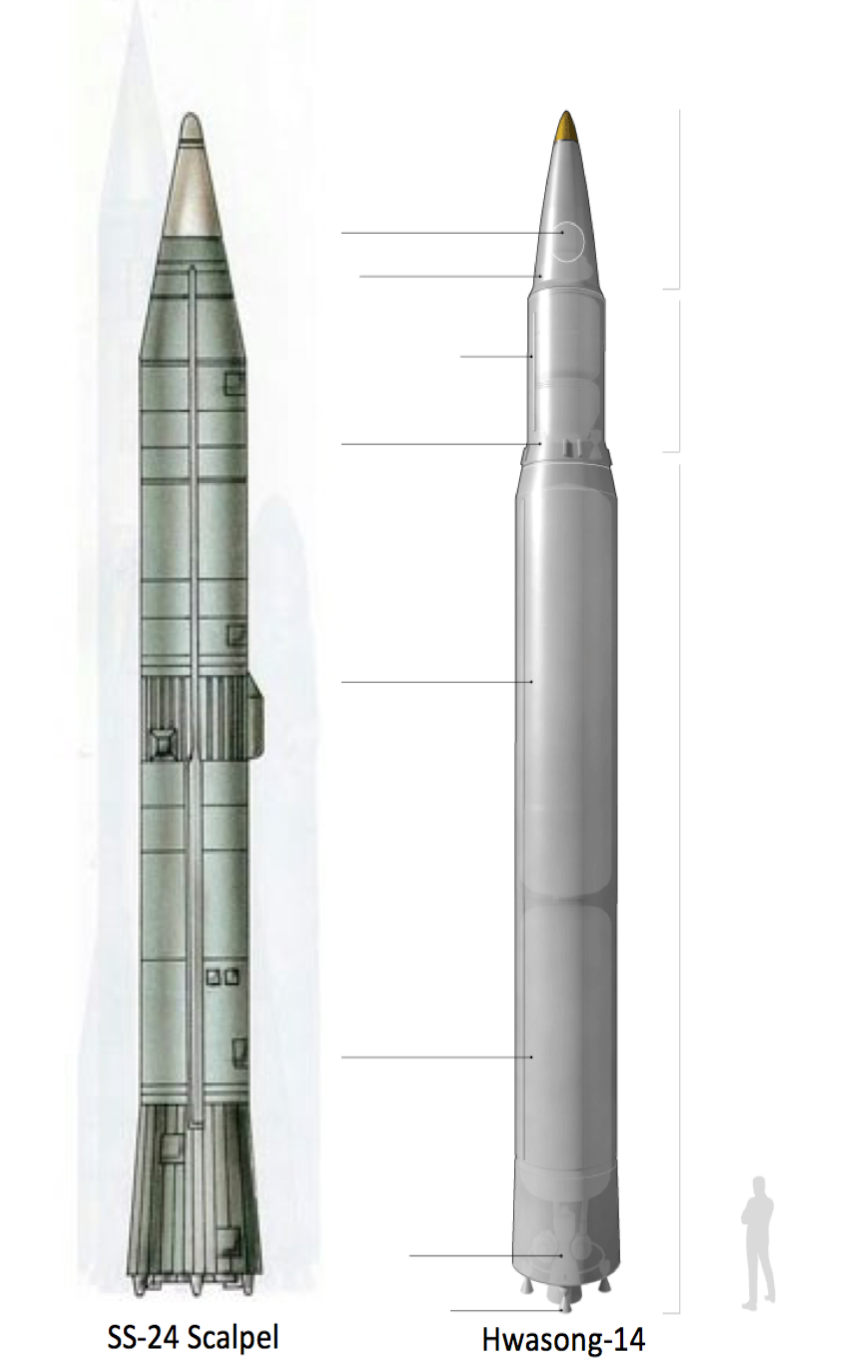
North Korea has become increasingly aggressive in utilizing its intelligence capabilities which creates an eminent national security threat. In 2011, Ukrainian security services arrested two North Korean spies in a sting operation for attempting to purloin nuclear design plans that contained instructions for developing an SS-24 Scalpel ICBM.7 It is feasible that the two spies were operating under the RGB given their level of training and specific assignment. While these plans were not leaked to the North Korean government, it is highly probable that other sets of plans were leaked out of either Ukraine or Russia. For example, North Korea used Russia’s exclusive high-performance liquid-propellant engine in their ICBM testing. Missile defense experts at the International Institute for Strategic Studies have determined that the design plans for the ICBM engine most likely came from an illicit intelligence network in either Russia or Ukraine.8 In addition to nuclear espionage, North Korea also utilizes its intelligence capabilities to conduct organized assassinations, most notably the assassination of North Korea’s Supreme Leader Kim Jong-un’s half-brother Kim Jong-nam. According to official reports, the two assassins were highly trained, and guided by North Korean agents.9 Additionally in 2010, North Korea sent two covert military officers into South Korea to surveil, and ultimately assassinate Hwang Jang Yop, former secretary of the North Korean Worker’s Party.10 All of these events indicate that North Korea is becoming increasingly more aggressive in the utilization of its intelligence collection capabilities.
The U.S. intelligence community should focus on deterring the North Korean intelligence threat without getting distracted by the more recent development of a concrete nuclear threat. Left unchecked, North Korea’s intelligence community development will almost certainly continue to advance the country’s nuclear capabilities. Kim Jong-un has made it clear that the development of nuclear weapons is key to the survival of his regime. Furthermore, the North Korean government has stressed that it is committed to the further development of nuclear weapons.11 In order to alter the course of North Korea’s nuclear development, the United States must prioritize counteracting North Korean intelligence forces and operations.■
- David Sanger. “North Korean Nuclear Test Draws U.S. Warning of ‘Massive Military Response.’” The New York Times. September 2, 2017. Web. 5 September 2017. https://www.nytimes.com/2017/09/03/world/asia/north-korea-tremor-possible-6th-nuclear-test.html
- “Kim Jong-nam: Who in North Korea could organise a VX murder?” BBC News. February 24, 2017. Web. 5 September 2017. http://www.bbc.com/news/world-asia-39073839
- David Majumdar. “North Korea’s Spy Agencies Should Not Be Underestimated.” The National Interest. April 23, 2017. Web. 31 August 2017. http://nationalinterest.org/blog/the-buzz/north-koreas-spy-agencies-should-not-be-underestimated-20319
- “Selected Supplemental Intelligence Service Information.” IOSS Intelligence Threat Handbook. Web. 31 August 2017. https://fas.org/irp/threat/handbook/supplement.pdf
- Ju-min Park. “Inside North Korea’s Unit 180, the cyber warfare cell that worries the West.” Business Insider. May 21, 2017. Web. 31 August 2017. http://www.businessinsider.com/r-exclusive-north-koreas-unit-180-the-cyber-warfare-cell-that-worries-the-west-2017-5
- “Experts Say It’s ‘Highly Likely’ North Korea Was Behind the WannaCry Ransomware Attack.” Fortune Tech. May 22, 2017. Web. 11 September 2017. http://fortune.com/2017/05/23/north-korea-wannacry-ransomware-symantec/
- Nick Walsh. “The North Korean spies Ukraine caught stealing missile plans.” CNN News. September 1, 2017. Web. 5 September 2017. http://www.cnn.com/2017/08/24/europe/ukraine-north-korea-spies/index.html
- Michael Elleman. “The secret to North Korea’s ICBM success.” International Institute for Strategic Studies. August 14, 2017. Web. 31 August 2017. http://www.iiss.org/en/iiss%20voices/blogsections/iiss-voices-2017-adeb/august-2b48/north-korea-icbm-success-3abb
- Richard Paddock. “Kim Jong-nam’s Death: A Geopolitical Whodunit.” The New York Times. February 22, 2017. Web. 5 September 2017. https://www.nytimes.com/2017/02/22/world/asia/kim-jong-nam-assassination-korea-malaysia.html
- Malcom Moore. “North Korean spies caught in assassination plot.” The Telegraph. April 21, 2010. Web. 31 August 2017. http://www.telegraph.co.uk/news/worldnews/asia/northkorea/7614075/North-Korean-spies-caught-in-assassination-plot.html
- Scott Bray. “Speech to the Institute for Korean-American Studies: North Korea’s Nuclear Weapons and Missile Capability.” National Intelligence Manager: East Asia. June 26, 2017. Web. 31 August 2017. https://www.dni.gov/files/ODNI/documents/20170726-NIM-East-Asia-Speech-to-ICAS-on-North-Koreas-Nulcear-and-Ballistic-Missile-Programs.pdf
Photo Credit:
North Korean Propaganda | http://imgur.com/O8o3Fqb
A comparison of the Russian SS-24 Scalpel and the North Korean Hwasong-14 | Adam Johnson
Spring 2017
Volume 20, Issue 5
17 May






